Ensuring only the right people access your company’s sensitive information is one of the most important goals of a modern business. Unauthorised access by hackers and even inappropriate access by legitimate users are both major threats to your company’s data integrity. You could even be legally liable for not having proper data protection policies. Fortunately, conditional access is one of the easiest, simplest, and cheapest ways to protect your data.
What is Conditional Access?
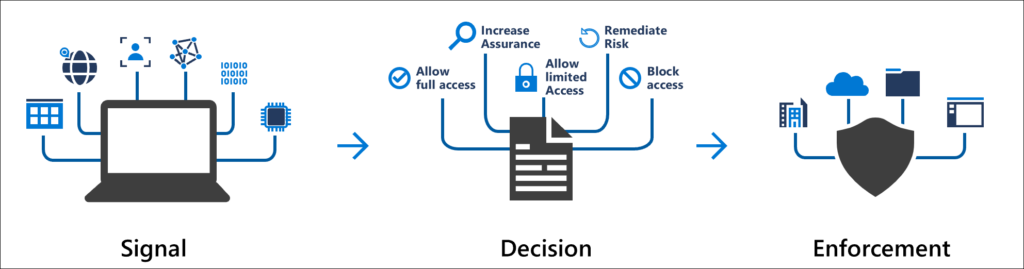
Conditional access is a security mechanism that controls which users access certain resources. You can set conditional action policies according to user identities, the devices used to log in, and other factors. For example, you could set a conditional access policy, such as only members of your accounting department having access to employee payrolls.
Conditional access policies work with simple statements. For example, if the user identity is “accountant”, then you can give access to the employee payroll. You can also set additional qualifiers like only giving access to payroll information to the accountant using a company computer during work hours for multi-factor authentication (MFA).
The benefit of conditional access policies is that they prevent unauthorised access to sensitive company data and improve your company’s cyber security.
What Parameters are used in Conditional Access
These are the five most commonly used parameters for conditional access policies:
- The user’s identity
- The user’s IP address
- The device used to access the data
- The user’s geographic location
- The time of day when the access attempt was made
Why Should you Consider Conditional Access?
Implementing conditional access provides your company with many benefits, including better security and a better user experience for employees.
1. Better Security
Conditional access can introduce multi-factor user authentication, which prevents unauthorised access to data. For example, a hacker from another country obtains your accountant’s login credentials. A contextual access policy would prevent them from logging into your system because it would detect they’re from another country.
That way, your company’s sensitive data is safe from a potential data breach. The multi-factor authentication element of conditional access allows only relevant people from an expected location with recognised devices to access your data.
2. Automation and Robustness
Since conditional access policies are built using if-then statements, they completely automate the entire process. You just set the policy according to your requirements, and the system executes them for you. That way, you save time and money by giving less burden to your administrative IT teams.
The best part is that automated processes are completely reliable and accurate. There’s no chance of human error once your desired policies are created. So conditional access helps ensure every login is verified and legitimate.
3. Context Awareness
Context awareness not only prevents unauthorised users from accessing your data, but it also helps restrict legitimate users. For example, you could set up your conditional access policies such that accountants can access employee payroll information, but they can’t access your employees’ confidential HR information.
This way, you’ll ensure there’s no chance of potential data misuse by anyone in your company. Your entire company’s data stays safe from potential abuse by people inside or outside of your company.
4. Better User Experience
Up to 67% of businesses don’t employ multi-factor authentication, even though it’s one of the easiest and simplest ways to stop unauthorised access. The reason why is because of the inconvenience that MFA brings. People don’t want to enter a PIN, a password and scan their fingerprint to access a single file. It costs time and reduces productivity.
These concerns are completely legitimate. Multi-factor authentication is inconvenient for many busy companies. Thankfully, conditional access can remove some of the inconvenience while still giving you the benefits of MFA. You can do that by setting conditional access with MFA on a context-basis.
For instance, your accountant tries to access employee payroll information from their home with their personal computer. Their reason for accessing the information is entirely legitimate, but the conditional access policies will note it’s an unusual device and location and suspect a hack. So it could request an MFA to confirm your accountant’s identity.
5. Have your employees only access to exactly what they need
The best security practice is to use the rule of least privilege, which means only granting necessary access to relevant users. Under this rule, you don’t give anyone access to information they don’t need. Conditional access is the best way to implement this rule since it simplifies the restriction process.
How Conditional Access Helps with Device Compliance
Device compliance refers to ensuring that your company’s devices, like laptops and smartphones, meet security and regulatory standards. These standards mostly include things like having updated software, adequate firewalls and anti-virus software, and employing proper data protection policies.
Conditional access helps your company achieve these goals by ensuring only devices that meet policies access your company’s data. For example, you could set the following device policies:
- Operating system: All devices must have an approved operating system.
- Security software: All devices must have approved firewalls and anti-virus software.
- Encryption: All devices must have encrypted hard drives.
- Remote wipe: All divides must have a remote wipe feature if they’re lost or stolen.
Implementing these policies helps businesses ensure only secure and regulatory complaint devices access company data. The policies also help prevent cyber security threats, like malware attacks and unauthorised access.
That being said, there can be a trade-off between increased security and employee user experience if the policies are too strict. The solution is to find the right balance between security and user experience for your company.
How Conditional Access Helps with Location Based Access
Location-based access is the ability of a conditional access system to prevent access to data because of a user’s geographic location. Think of our previous example when a hacker from another country tries to log in with your accountant’s credentials. There are also many other ways that conditional access helps with location-based access.
For instance, you can set policies that prevent users from accessing sensitive data outside the office. This is useful if you don’t want your accountant accessing employee payroll information outside of the office.
You can use the three following ways to track a device’s location:
- IP address: IP addresses are the most reliable way to access a device’s location, but they can sometimes be faked. It’s best to use IP address tracking with these other two location tracking methods.
- GPS: A device with GPS capabilities can provide its exact geographic location. The conditional access system would request the device’s GPS location and grant access if it’s from an approved location.
- Wi-Fi: You can detect a device’s location according to the location of the Wi-Fi network it’s using. For instance, using office Wi-Fi means a device is in the office.
Applying these location-based access policies ensures that only approved devices from approved locations access your company’s sensitive data. This prevents data breaches because of devices being lost or connected to unsecured networks.
How Conditional Access Helps with Timed Based Access
Time-based access is the ability of a conditional access system to prevent access to company data based on the time of the attempted access. You can use conditional access to prevent access to sensitive data outside of normal working hours. Conversely, you could also ensure that access to sensitive data is restricted only during specific times.
For example, your business may want employees to only access sensitive customer data during a meeting with that customer. Conditional access ensures your employees only access the customer data at the approved time.
You can apply time-based policies for specific users, groups of users, specific resources, and even specific devices. In any case, implementing the correct policies ensures that company data is only accessible at approved times, which prevents data breaches and helps you meet regulatory requirements.
How to implement Conditional Access for Small Businesses
Conditional access policies help small businesses by protecting their data against cyber security threats. It does so by controlling access to resources according to specific conditions.
You can use the following four steps to protect your company’s data with conditional access policies:
1. Identify your company’s most sensitive data
This is the data that’s most important for your business. It could be your intellectual property, financial data, customer data, or similar sensitive information.
2. Assess the risk of unauthorised access to your most sensitive data
Find out how easily someone could gain unauthorised access to your data. Doing so helps determine how much security your company needs.
3. Use cloud-based security tools
Ideally, purchase a professional cloud-based storage service package and use reliable security tools to protect your data.
4. Routinely monitor access to data and enforce conditional access policies
You should regularly confirm only authorised users access your data from secured devices and approved locations.
Conditional access policies are a great way to improve your company’s cyber security, but they can be complicated to create.
Finally, you could contact a managed service provider (MSP) such as PowerbITs, to create your conditional access policies for you. Click here if you’d like a free consultation today.