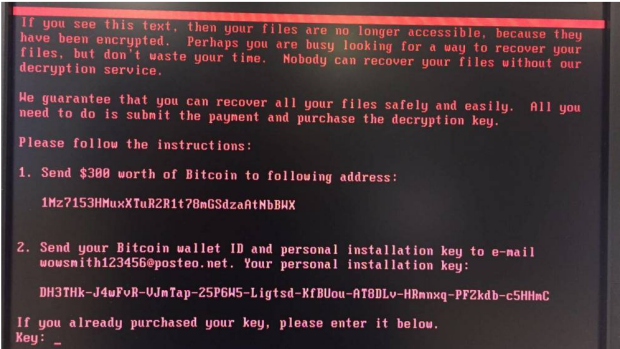
Users of Windows need to be notified ASAP of a new ransomware strain and take immediate measures to patch.
A new major ransomware cyber attack is unrolling worldwide and leaving chaos in its wake. Global US firms have been affected, but most incidents are being reported out of Europe—and especially Ukraine. There, government ministries, banks, utilities, critical infrastructure and companies nationwide have been targets. For many, operations are forced to a standstill.
The malware believed to be used is a variant of a strain first introduced last year called Petya, which was updated to overcome fixes put in place to protect against it. The new malware name: Petrwrap. At this point, it’s unclear which version might be the culprit.
Regardless the new ransomware is tied to WannaCry, with several security firms confirming that it uses the same Windows vulnerability to spread through computer systems. First revealed publicly in April, this vulnerability known as Eternal Blue was patched by Microsoft in March, so any computer set to automatically install security updates is protected.
For businesses, the specific security update needed to protect against Eternal Blue is MS17-010. In line with Microsoft’s guidance from 2016, businesses unable to patch should consider disabling SMBv1 and other legacy protocols to prevent the infection spreading.